Protecting Your Digital Privacy
A phone and computer are arguably the two most used devices these days. We use them regularly every day and most of us even work with them for several hours in a row or even for a whole day.
Human beings love speed. We all sacrifice privacy, a lot of it, for speed. We do not set up password/pin protection on our devices to save time as we unlock them and we let applications use our location data indefinitely to save us a little bit of time in future so that application does not ask about it again.
Many applications tend to misuse permissions by asking for more than they need.
For example, a torch application should not really need access to your photos or location, right? Speaking about location, apps tend to ask for access to your location not only while using it in the background too, even when the device is idle.
Another big thing is browsers - software that we use most frequently to access content over the Internet. Most browsers send data without our consent and allow websites to store cookie files with unique identifiable information.
How many times have you experienced Deja Vu after looking up a product and later finding ads for that product all over social networks and contextual ads everywhere?
Cracked applications and unofficial app stores are dangerous too. No one checks the validity and honesty there and attackers often leverage this possibility heavily. Sticking with the official app stores is essential.
And the public networks? We love free Wi-Fi but it comes at a cost - open Wi-Fi network means the data transmitted is not encrypted and attackers may be able to eavesdrop and hijack important sensitive information such as passwords or photos.
Have you seen laptops with webcam covers? There is a real reason people concerned with privacy use them.
Your Phone
Mobile phones of today are tiny powerful computers - they have tons of storage and processing power available at their disposal and because of portability, ease and frequency of use, there are tons of productivity applications available for smartphones, not seen on a personal computer.
Mail, messaging, chat apps, wallets, banking software, personal notes, photos and videos are just a tiny example of what we use or store on our phones. The increased attack surface of smartphones attracts a lot of malevolent interest to them.
Let us touch on some ways of privacy compromise in detail.
- Password/PIN protection is the absolute essential - without this your phone is like an open house, inviting anyone to get their hands on whatever they wish.
- Applications from unofficial app stores are dangerous too. No one checks the validity and integrity there and attackers often leverage this possibility heavily. Sticking with the official app stores is essential, for any operating system.
- Cracked applications are another source of privacy compromise. Cracks often include malware undetectable by antivirus and antimalware software which gives attackers the possibility to even take over your device and eavesdrop on you.
- The so-called jailbreaks are dangerous too because they disable many of the device’s security measures and open the core of it for apps to be more accessible.
- Free Wi-Fi comes at a cost - open Wi-Fi network means the data transmitted is not encrypted and attackers may be able to eavesdrop and hijack important sensitive information such as passwords.
- And normal software, such as browsers can be used to alter your privacy too.
Apart from that, there are other more sophisticated and dangerous methods that can be used to track people on mobile networks, not depending on any security measure the user takes on his or her end, not to mention turning off the phone itself, of course.
One of the scariest is a hack that uses a network interchange service called Signaling System No. 7 (SS7).
Successfully exploiting it, the attacker can read text messages, listen to calls and track a smartphone based on mobile phone mast triangulation, using only a phone number as an identifier.
Using full device encryption is also a must to avoid any data breach in case of device theft. Both popular operating systems, iOS and Android offer the options for it.
Your Computer
Enabling full disk encryption is a great way to protect against data leaks.
Every operating system offers such a possibility and you can use BitLocker on Windows and FileVault on Mac OS X to do that.
Linux flavors also offer a variety of possibilities in this sphere and you can always use a multi-platform solution like VeraCrypt, which can also be used to encrypt individual files, containers or create encrypted volumes too.
Turning off and/or covering your microphone and webcam is also a good practice. There is a real reason people concerned with privacy use webcam covers.
But the most dangerous are malware, particularly on Windows operating system. As it is the most widely used OS, attackers get most benefits targeting Windows, rather than other systems. You should always be careful with unknown files and use security best practices and updated antimalware software to keep yourself safe.
Ways to Protect Your Digital Privacy
The following are strategies and tools you can use to protect your digital identity.
Strong Passwords
Reusing the same password on many websites and applications is the number one security bad practice.
Even large and strong platforms are being hacked and their users’ credentials are sold over black markets. There have been cases when the stolen data was available publicly too. Imagine if your credentials were in one of these databases - every account you used the same password for, is essentially hacked too.
It is important that you use a different password for each website or application you create an account for.
Consider this the number one security best practice.
The second best practice is creating passwords that are strong and hard to guess, especially for computers, but for humans too.
Let’s compare these two passwords:
- Tr0ub4dor&3
- correcthorsebatterystaple
The first password is very hard for a human being to remember but it can be easily brute-forced using modern hardware, therefore it is easy to guess for a computer.
Now the second password is very easy to remember as a human being but it is amazingly hard for a computer to bruteforce it. It will take hundreds of years to crack it.
As we have learned the two basic rules now a third problem arises - we have so many accounts nowadays! How can a normal human being remember so many different passwords? One cannot, obviously.
Password managers come to save us. These programs manage passwords for us so that we don’t even have to remember them. Amazing, right?
Using password managers means you can also generate long, complex passwords and do not worry that either a human being or a computer can crack or remember it. You can even generate random data for security questions and save them in the software vault itself.
It comes at a cost though - now you have a single point of failure so you have to choose a strong password and protect your password manager vault very carefully.
How Are Passwords Hacked?
There are a few well-known methods used by hackers to obtain a password. The easiest way for a hacker to do so is through phishing.
With Phishing, an attacker tries to get you to hand out your password willingly. This can be done by sending you an email asking you to verify your account. A link in the email might take you to a website that looks just like the original website the email claims to link to.
By entering your login information on this duplicate fake website the hackers have achieved their goal.
When you receive a suspicious email like the example above, please do not click on any links.
If in doubt, visit the website as you normally would and check your account for notifications requiring users to verify their credentials. If you do not have a notification, the email is most certainly a scam.
If an attacker cannot get you to tell them your password through trickery they have two more options.
- Dictionary Attack - In a dictionary attack, the hackers try a large number of common words, e.g. from a dictionary. They will not only use regular words from your Oxford Dictionary but also the most common passwords. In case some of your passwords are along the line of Password123, P4ssword, P4ssw0rd or Thisismypassword you are highly vulnerable to such an attack.
- Brute Force Attack - A brute force attack focuses on your password. Although an attacker will only use this method if you are the only target. During a brute force attack, the hacker will try out every possible combination of characters, numbers, and symbols until the attacker gains access to your account.
The attacker will most likely combine the dictionary and brute force attack by first trying out the most common passwords before moving on to random guessing.
What a Password Should Look Like
- A strong password should have at least 12 characters.
- If you are protecting sensitive information, use 20 characters or more
- Use a mix of capitalized and regular letters, numbers and symbols.
- Don’t just use symbols or numbers as a replacement for letters as in pa$$word or p4ssw0rd.
- To an automated attack, the passwords are just as trivial as the original word.
There are some methods that you can apply to create a strong password.
The sentence method uses a familiar sentence as a starting point and applies some sort of algorithm to make your password.
You could start out with “I went to school in Woodland Park and played soccer during fall season”.
Now you can think of an algorithm to create a password out of this sentence, like using the first two characters of each word, the last two characters, the first and the last or any other combination that works for you.
Using the first two characters would yield:
IwetoscinWoPaanplsodufase
This is a fairly secure password that will survive both a dictionary attack, as well as a brute force attack if the attacker is not 100% committed to you as a target.
Another method is using regular words that don’t make sense in this combination.
correcthorsebatterystaple is a commonly used example of this method.
How Do You Remember These?
The difficult and less secure method would be to add some sort of code to the end of a standard password, depending on the account you use it for.
This way you could use:
- “IwetoscinWoPaanplsodufase_fcbk” for your Facebook account
- And “IwetoscinWoPaanplsodufase_amzn” for your Amazon Login.
There have been many incidents of password databases being hacked and this method would make you vulnerable to such a data breach because the attackers could derive your other passwords if they figure out the scheme you used to adapt the password.
A better method is to use a password manager that generates long and difficult to guess passwords and saves them for you. Now you only have to remember one super strong password to protect your password manager application and you are good to go.
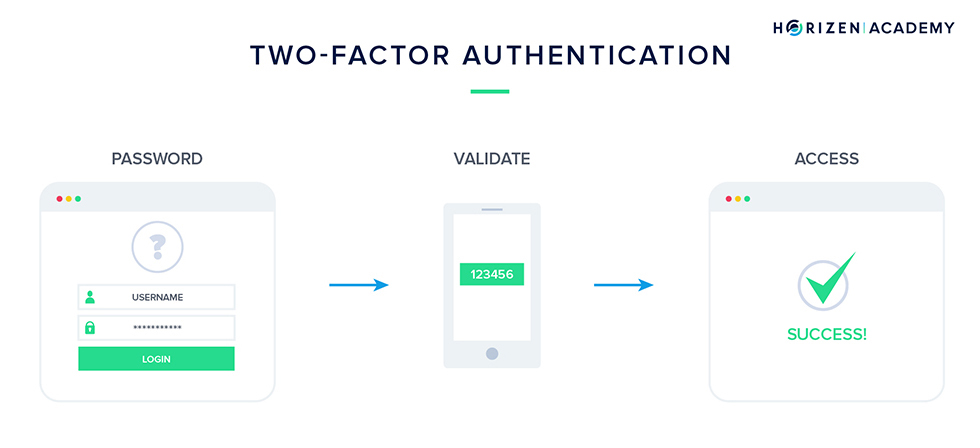
2FA - Two-Factor Authentication
Two-factor Authentication or in short, 2FA, is a way to let users access a service using a combination of two authentication methods.
This may be an additional:
- PIN code or a password
- A one-time password (OTP)
- A fingerprint or other biometric data
- Or even an additional security chip or token inside your device.
We already use 2FA in real life.
A notable example is using an ATM to withdraw cash using a debit card and a PIN code.
However many services use only one-factor authentication for user identification and that one factor is obviously a password.
The good news is that almost every service in a blockchain world has an optional 2FA built in. It became a de-facto standard in this sphere.
Enabling 2FA is one of the best security best practices you can employ as it protects you even in cases of platform-level hacks when the passwords get exposed. Of course, considering that the platform itself has the 2FA implemented correctly.
2FA works by requiring you to prove your identity by a secondary method of authentication in addition to your password.
Most commonly the secondary method of authentication is an SMS message sent to your phone number or a code generated on a dedicated application, like Microsoft Authenticator, Google Authenticator or others.
2FA Through Text Messages
We advise you not to use text messages as a 2FA method if possible. There is more than one way an attacker can access text messages or calls your phone is receiving.
The first and most simple method is social engineering.
There have been a number of incidents where an attacker managed to convince an employee of a mobile communications company that “his” phone got lost or his SIM card broke and that he needs a replacement immediately.
Coincidentally the victim also just moved, so the address is changed and a second SIM card is shipped to the attacker.
Although this exploit is unlikely to work on the first try, by repeatedly calling the service hotline of a phone company eventually the attacker might find an employee willing to do just this.
Another method the attacker might use is to open an account with a different service provider and request your number to be ported.
Most providers offer you to keep your number if you switch from let’s say Verizon to AT&T. This opens up this simple but effective attack vector.
We could go on with the list of possible exploits but the point is: your number is a rather easy target.
2FA Applications
Using a separate code generating application is important because you can use it offline or in another country without turning on a roaming service. You can also be sure that no one takes over your mobile number and gets an SMS before you or alters it in some form or another.
2FA comes with a drawback. You become dependent upon it, and like your password manager vault, you have to be careful not to lose your second-factor authentication device which in most cases is your smartphone.
Thankfully, many 2FA applications and services offer a way to back up the application itself or keep a backup code for the service itself so that you are not locked out permanently.
If you don’t trust a Google application to take care of your 2FA, there are a large number of similar apps.
If you want to take it one step further, you can use a hardware device such as the YubiKey or even the Ledger Hardware Wallet that can store your cryptocurrencies, as well as providing you with 2FA capabilities through FIDO U2F.
Most methods offer a way to restore your 2FA codes, in case you accidentally delete the app, your phone breaks or you lose your hardware authenticator.
Make sure to familiarize yourself with the backup procedure for the method of your choice before you start using it, so you are not caught off guard in such a situation and lose access to your accounts.
The "Nothing to Hide" Argument
The Nothing to Hide argument states that:
Government surveillance programs do not threaten privacy unless they discover illegal activities. And, if they do discover illegal activities, the person responsible for activities does not have the right to keep them private. Therefore, a person who is in favor of this argument may state - they've got nothing to hide - and therefore doesn’t express opposition to government oversight and surveillance. Individuals using this argument may express that a person should not worry about government or surveillance if they have “nothing to hide.”
We think this argument is very flawed because:
Privacy is not about hiding, it is about protecting: Would you give passwords to your email and other accounts to anyone? Would you allow everyone to read your social media messages? Would you love to have someone always around who eavesdrops on each and every conversation of yours, see your medical records and know about your appointments with your doctor? Or let's go very trivial - why do you ever have curtains on the shady side of your house or even wear pants?
Privacy is a fundamental human right: The right to free speech and the right to assemble are the basic fundamental human rights even if you do not have anything to say or protest now. So is privacy. Think about voting, medical information, and banking information. It is obvious that you wish them to be kept private.
Lack of privacy is harmful: You might get discriminated against or harassed based on your personal information or become a victim of identity theft or impersonation.
Location data is sensitive: It can determine where you live, where you work, where you shop and hang out with friends. Every modern smartphone detects home and workplace just after several days of usage.
Social media gathers even more: What you like or follow and what applications you use on social media determine what types of ads you will see. Your age, sex, occupation, job title, and every other little detail can also be taken into account for ad targeting. Social media is the best marketing platform we have seen to date. Not only do those details determine what kind of ads you see, but sometimes also what price is shown to you. Especially when you book flights your metadata determines what prices will be available.
Every little bit counts: Some companies gather emails while others locate where you go shop or eat. Some large search engines even keep your search history if you use their account. Others aggregate all the data and form a complete picture of who you are, where you go and with whom and what you do. As the great article over spreadprivacy.com says - If that feels creepy, it’s because it is.
The “nothing to hide” argument is flawed and irrelevant today.
People who think they have nothing to hide essentially say that they are so harmless and uninteresting of a person that it means nothing for them if someone eavesdrops on their lives constantly, which, if explained in detail, will obviously be unacceptable.
Even though privacy is being invaded left and right, you still have the power to protect it in many ways.
There are simple steps you can follow to regain control and dramatically increase your privacy level:
- Encrypt emails, messages, and calls
- Change privacy settings on your devices and software
- Use different, more private tools and applications
- Learn more about privacy protection techniques and advanced methodologies
Tools to Protect Your Privacy
Password Managers
It is essential to have a different password for each service and application you use. That raised the question, “How can a normal human being remember so many different passwords?”, and the solution for that question is Password Managers.
These programs manage passwords for us so that we don’t have to.
It is also essential to know that password managers need a master password, one that decrypts your vault and unlocks all others. The master password must be a very secure one but also easy to remember. Many password managers offer and recommend the use of 2FA.
There are three types of password managers: locally installed software applications, online services accessed through website portals, and locally accessed hardware devices that serve as keys.
The most useful for beginners are web-based services. These services sync passwords between your devices and keep your vault secured in the cloud, and protected with a master password and 2FA (preferably).
Most of these password managers have browser add-ons and/or software available to install on your computer or mobile device and acts as a vault.
It is important to take note of pricing. While many password managers offer paid tiers, some have excellent free versions available e.g. LastPass. We recommend starting with a free tier or trial, testing things out and deciding if the specific password manager fits your needs.
You might discover that a free tier is satisfactory for you or you may wish to upgrade to the paid one as needed.
The hardest part is choosing a password manager itself - there are so many of them! Rather than choosing a specific one for you, we encourage you to try several and only then choose the one best suited to your needs and devices.
Some popular ones include:
- LastPass
- 1Password
- MasterPass
- KeePassX
Browsers
Browsers - the software that we use the most frequently to access content on the Internet are the scariest ones. Most browsers send data without our consent and allow websites to store cookie files with unique identifiable information.
How many times have you experienced Deja Vu after looking up a product and later finding ads for a product you were looking at only to find that product all over social networks and contextual ads everywhere?
Choosing a privacy-preserving browser and altering the settings accordingly is an essential part of our private journey through the Internet.
Today there are browsers available that either offer good privacy features out-of-box or can be adjusted accordingly:
First, Tor. In short, apart from a browser itself, Tor is free software and an open network to help you defend yourself against network surveillance and traffic analysis.
Brave is a free and open-source web browser developed by Brave Software Inc. based on the Chromium web browser which blocks ads and website trackers by default.
And as for Mozilla Firefox, which is a very popular one, you need to adjust privacy settings to make it a more privacy-friendly app, but don’t forget to adjust the privacy settings.
There are browsers with privacy add-ons available, like Privacy Badger for Chrome and Opera (also for Firefox). These add-ons enhance the privacy experience and make your favorite software to access the Internet less sneaky.
Unfortunately, most browsers pass “fingerprints” that enable websites to track them by the configuration and settings information. There is also a Do Not Track header available for browsers to broadcast to websites, signaling them not to track users but many websites do not honor that header.
Protecting against fingerprinting entirely is difficult and the only fully working solution is using Tor. With other browsers using an add-on, like Privacy Badger, can improve security. Another powerful mechanism to defend against fingerprinting is disabling JavaScript - it essentially cuts off the methods that websites use to detect things like fonts and plugins.
Unfortunately, JavaScript is also needed to make most websites work correctly.
Search Engines
You might have heard that major search engines track their users and those stories are right.
It is no secret today that search engines like Google, Bing, Yahoo! and others track almost 100% of search queries you do and tailor the results you see on your screen specifically for you.
In other words, they give you personalized results. On the other hand, your search data is being exploited to serve relevant ads to you while you browse the Internet.
As most of us use Google for our searching needs, there is a big chance you do too.
Head over to your Google activity to have a look at your activity across different Google services and get amazed at how much data is being gathered about you.
It is also worth mentioning that to abide the modern regulations Google and others offer the option to delete your history and it is recommended that you use this feature regularly, to prevent the accumulation of massive data about your activities.
We recommend two search engines that preserve your privacy:
DuckDuckGo
DuckDuckGo is a very popular privacy-protecting search engine. They deliver results with "quality over quantity" in mind. DuckDuckGo does not track you or serve ads and does not filter search results. They also provide an application for iOS and Android and an extension to Chrome for such added functionality as blocking trackers, encrypting traffic and so on.
Startpage
Startpage is a very user-friendly search engine which uses Google's search results, removes all tracking information and serves it to you. Using Google's results makes it familiar and the results are also high in quality.
Startpage does not keep any relevant information regarding you so they state that they are not afraid of anyone because they have nothing to hand over to them.
Another wonderful feature of Startpage is Anonymous View in which it proxies you to the website so that your computer is not barraged with cookies. Startpage does not filter the results either, so no tailored and personalized searches there.
Ad Blockers
We talked about browsers, software used to access content over the Internet and mentioned that there are some add-ons available that help enhance your privacy experience. Let’s talk about the most notable ones:
- Privacy Badger - This add-on inhibits tracking from advertisers. Privacy Badger also learns as you surf - if an advertiser seems to be tracking you without your permission across multiple websites, the add-on automatically blocks him from showing more content.
- uBlock Origin - It works similarly to a wide-spectrum blocker. It uses Origin’s own filter list and lists of other similar add-ons including EasyList, EasyPrivacy, Peter Lowe’s ad/tracking/malware servers, and various lists of malware sites.
- AdBlock Plus - Possibly the most popular ad-blocking add-on. It blocks annoying ads, disables tracking, and blocks domains known to spread malware. AdBlock Plus has an Acceptable Ads list which displays ads that comply with the acceptable ads criteria agreed upon by the community of users. The list is maintained by Eyeo GmbH.
- HTTPS Everywhere - It encrypts traffic between you and many websites, essentially making your browsing more secure. Many websites still use HTTP unencrypted links inside HTTPS content. The HTTPS Everywhere extension rewrites the requests for these sites to HTTPS.
There are many add-ons available for these and other browsers to enhance your private browsing experience. Just be careful and do your own research - many add-ons might not be doing what they are advertising.
VPNs
Usually, you are at risk of having the data you are sending and receiving intercepted when you are using an unsecured public network like with a Wifi hotspot in a cafe or at an airport.
By using a Virtual Private Network (VPN) you can rest assured that the entire communication between your computer and the endpoint of your connection is protected. A VPN will encrypt all the data you are transmitting on your device and decrypts the data when it reaches its desired endpoint.
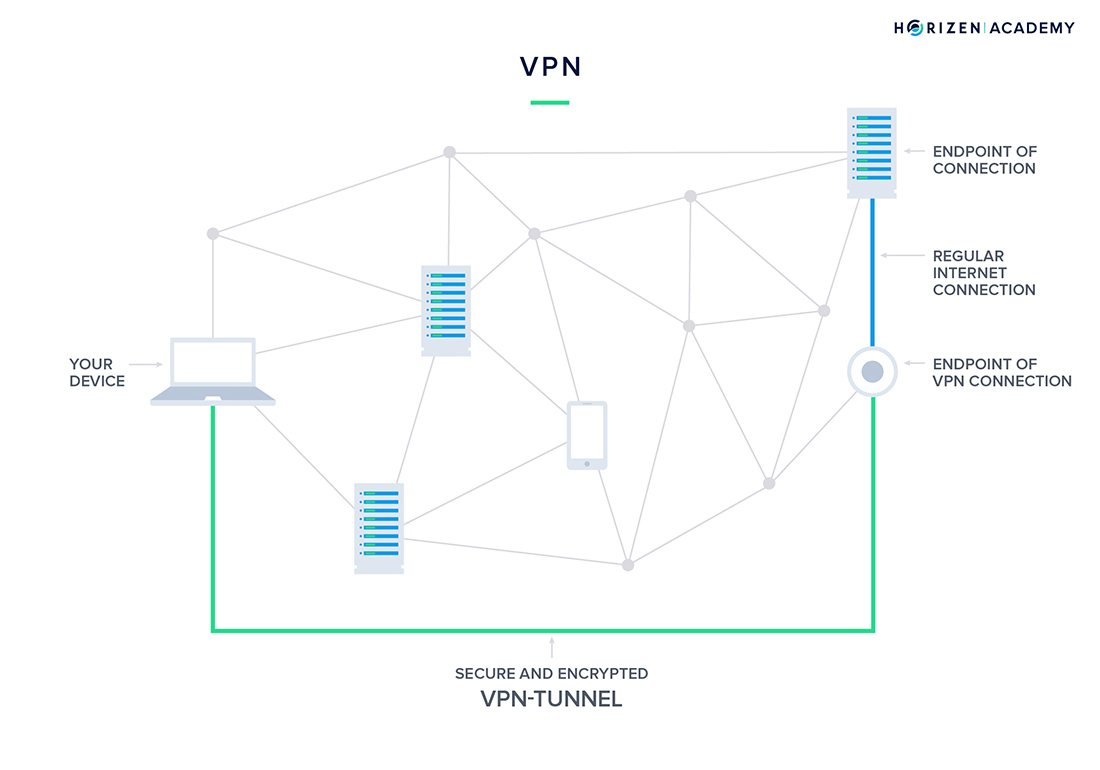
A VPN is a secure tunnel between two or more devices.
A VPN secures your connection just like if you were using a private network. For example, many companies require their employees to use a VPN to access the private office network when they are working remotely.
This ensures the data is as secure as if they were on site without the risk of data leaks.
VPNs also allow you to access services that are normally blocked in your region. You can "pretend" to be somewhere else to connect to a service not typically available in your area.
Doing this allows you to connect to an endpoint that is within the area that the service you want to use is serving. If you connect to an endpoint in the United States, nobody can tell where the connection originates from.
Especially people in countries with authoritarian regimes tend to limit access to the world wide web. Not only do they block certain services like streaming websites or social networks, but sometimes they also limit access to basic information that should be accessible to every person in the world.
Choosing a VPN
Choose a VPN that is not based in one of the Fourteen Eyes jurisdictions.
These jurisdictions include Australia, Canada, New Zealand, the UK, and the US (Five Eyes) as well as a few more European countries like Germany, France, and Sweden.
These jurisdictions have formed an alliance to collect and share mass surveillance data. These countries might require VPN providers in their jurisdictions to share data about their users.
Next, pick a VPN provider that doesn't require personal information to register as a user. You should not need more than an email address to use their service. Personal information also includes payment details.
To maintain the highest level of privacy possible choose a VPN service which accepts cryptocurrency, cash cards or debit cards.
Encrypted Email
For a sophisticated hacker, it is incredibly easy to intercept your emails if you are the target. The easiest way to get your hands on somebody else’s email is to gain access to that person’s email account.
If you follow the best practices we introduced earlier, namely choosing a secure password for your email account and activating 2FA, this becomes much harder already. Still, there are ways to intercept your email traffic.
Using unsecured wifi networks is another attack vector for an adversary to access your online correspondence. Encrypted emails resolve this problem and are much easier to use than one might think.
How to Start?
There are generally two options to choose from if you want to start using encrypted emails.
The first and maybe a more convenient option is to use add-ons for your existing email accounts and clients.
There are add-ons for email service providers such as Gmail. Apple Mail and Microsoft Outlook natively support encrypted emails.
The second and maybe a less convenient option is to switch to a secure email client.
These clients such as ProtonMail, CipherPost, Hushmail, or Disroot support email encryption natively from the regular interface. Most of these privacy-centric email providers will support the OpenPGP standard, which is open source and free.
It’s important to note that exchanging encrypted emails only works with people that have set up their encryption as well, either by using an add-on or by configuring their email managers. You need to exchange your public keys before you can address an encrypted email to somebody.
So, Which One to Choose?
That is a question that only you can answer. The first question you should ask yourself is how sensitive your data is. If you wish to communicate privately but don’t have to worry about harsh consequences in case your email correspondence were to become public, an add-on for your existing email will probably do the trick.
In case you are actually dealing with sensitive information regularly, you should consider switching your email provider or at least creating a second email address for sensitive content.
Since you want to protect your privacy, be careful about how much personal information the service provider is requesting during the signup procedure. Make sure you use a strong password and enable 2FA.
All of the following providers have a free service and accept cryptocurrency for premium accounts.
Paying with cryptocurrencies or cash cards avoids sharing your banking details or credit card information with the email provider
Messaging
We all chat and we do tons of it.
SMS, iMessage, Skype, Messenger, WhatsApp, Telegram… Some might even remember the era of ICQ and mIRC!
Texting/messaging is a very comfortable medium to use because it doesn’t require an immediate reply and you can use it in non-private and noisy environments. Integrated voice messaging is another useful functionality to use when you are in a hurry and want to save time.
We use these messengers often, but it also raises a question about privacy. How is the data is being kept, treated, and transmitted? Are we protected while sharing private data over these applications?
Well, it turns out some do it quite well while others not so much.
As in many other things, privacy comes at the cost of comfort. The more privacy-focused the application, the more limitations you might find there.
The most important feature for the modern day messengers is arguably the end-to-end encryption, which means that data is encrypted during transmission and is not sent as cleartext.
It is important to pay attention to such things as company and infrastructure jurisdiction, implications in giving customers’ data to intelligence agencies, surveillance capabilities built into the app, the collection of customers’ data, cryptographic primitives, are the app and infrastructure open source or not, and can you sign up and use the application anonymously or not.
Let’s go over some of the most privacy protecting messaging applications:
Ricochet Refresh
Although an experiment according to its author, Ricochet uses the Tor network to reach your contacts without relying on messaging servers. It creates a hidden service to rendezvous with your contacts without revealing your location or IP address. Instead of a username, you get a unique address that looks like ricochet:rs7ce36jsj24ogfw.
Other Ricochet users can use this address to send a contact request by asking to be added to your contacts list.
You can see when your contacts are online, and send them messages (and soon, files!). Your list of contacts is only known to your computer - never exposed to servers or network traffic monitoring.
Everything is encrypted end-to-end, so only the intended recipient can decrypt it, and anonymized, so nobody knows where it’s going and where it came from.
As for more conventional messaging applications, some of the most notable ones with privacy preserving features include Signal, Threema, and Wire.
securemessagingapps.com has a great comparison of these apps along with some others which are very popular and frequently used like Telegram, Skype, WhatsApp, Messenger, and others.
Rather than explaining everything again here, we recommend that you go over there and compare apps using the table at the website.
Keybase
Teamwork and collaboration is another big thing today with Slack and Teams leading the pack. In case you need a privacy-preserving teamwork application, Keybase is quite a nice alternative.
According to its own website:
“Keybase is a new and free security app for mobile phones and computers. For the geeks among us: it’s open source and powered by public-key cryptography. Keybase is for anyone. Imagine a Slack for the whole world, except end-to-end encrypted across all your devices. Or a Team Dropbox where the server can’t leak your files or be hacked.”
Virtual Phone Numbers
A virtual phone number is a number on the internet and is also known as direct inward dialing (DID).
The primary function of a virtual phone number is to forward calls to your primary phone number. The caller will never learn your actual phone number during this process. A virtual phone number enables you to have several numbers, in several countries without having to deal with multiple sim cards and service providers.
Many virtual phone number services also offer more sophisticated functionalities like recording calls, holding virtual phone conferences, texting or allowing for voicemail.
If you have ever called a service line that asked you to “Press 1 for Support, press 2 for general inquiries…” and so on, this company most likely uses virtual phone numbers.
Once the service line collects all the necessary information from the customer, the system forwards the call to the appropriate employee. You can structure the system to forward some calls to a cell phone instead of a landline in a call center.
The benefit for companies using such a system is an immense reduction in cost. To achieve this goal on an enterprise level, a company would have to buy a lot of hardware and register a large number of phone numbers with a telecommunication company.
With virtual phone numbers, they can set up a complex structure of different numbers forwarded to the right employee.
Another benefit is that they can serve customers from different countries without having these customers call an expensive foreign number.
Privacy Through Virtual Phone Numbers
When you register for a service or platform you are oftentimes asked to provide a valid phone number. There are legitimate reasons for not wanting to share your private number this way. By using a virtual phone number you can freely hand out a number to any service.
If you receive unwanted calls you can either block the caller ID, or change your number altogether. It works just like a burner phone would.
Virtual phone numbers also allow you to mask your location. The virtual phone number forwards calls over the internet. If you pick the right provider, nobody will ever know what place a call is actually forwarded to.
Using a Virtual Phone Number
First, you will need to pick a service that suits your needs. There are different options depending on how long you want your number to be available, how many numbers you would like to have simultaneously and which additional features like texting or voicemail you need.
Second, watch out for services that require your personal information to sign up for a virtual phone number. The whole point is to keep your private data to yourself, so be wary if the service provider collects more data than they need.
Some services don’t even require you to provide your phone number and use their app to forward messages and calls to you.
Lastly, you should pick a service that you can pay for privately. Using cryptocurrencies or cash cards saves you from revealing more personal data than necessary.