What is Crypto Mining?
Not every blockchain has miners. Only in Proof of Work is there mining, and therefore, miners.
They work to secure the blockchain against attacks and protect the history recorded against changes.
Mining is more than just performing Proof of Work, it comes with highly interesting economic implications, from choosing which blockchain to mine, to what hardware to use and what strategies to apply.
We will often use the term decentralizing and centralizing to express in which direction a given development shifts the overall level of coordination. There is no absolute decentralization or centralization and a system is moving on a scale between the two.
What is Mining?
Mining is a part of coming to a consensus on a blockchain that uses the Proof-of-Work method to agree on the order of transactions.
A miner records every transaction that happens on the blockchain. Two different miners might have different versions of the transaction history.
Every miner writes everything she recorded on the blockchain in a block. Since there are many miners on a blockchain, there are many different versions for the same block. They differ in the exact order of transactions.
All the miners have to solve a difficult computation that requires a lot of processing power.
The miner who solves the problem first gets to add her block to the blockchain.
The winning miner’s opinion will become the truth accepted by everybody else on the network, based on her solving the computation first.
How Does Mining Work?
Mining describes the activity of performing a computationally expensive task - the Proof of Work (PoW).
In the simplest case, this task is finding a nonce that when hashed together with the rest of the block header produces a block hash below a certain threshold which is called the target.
The total number of hash operations performed per second is called the hashrate of the network.
This type of PoW is called Hashcash Proof of Work and was introduced by Adam Back in 1997 as a measure against spam emails.
The idea is simple: Adding a small PoW to an email does not impact an honest user sending only a few mails per day. Automated spam on the other hand would become computationally expensive because every single email would need to have a valid PoW attached.
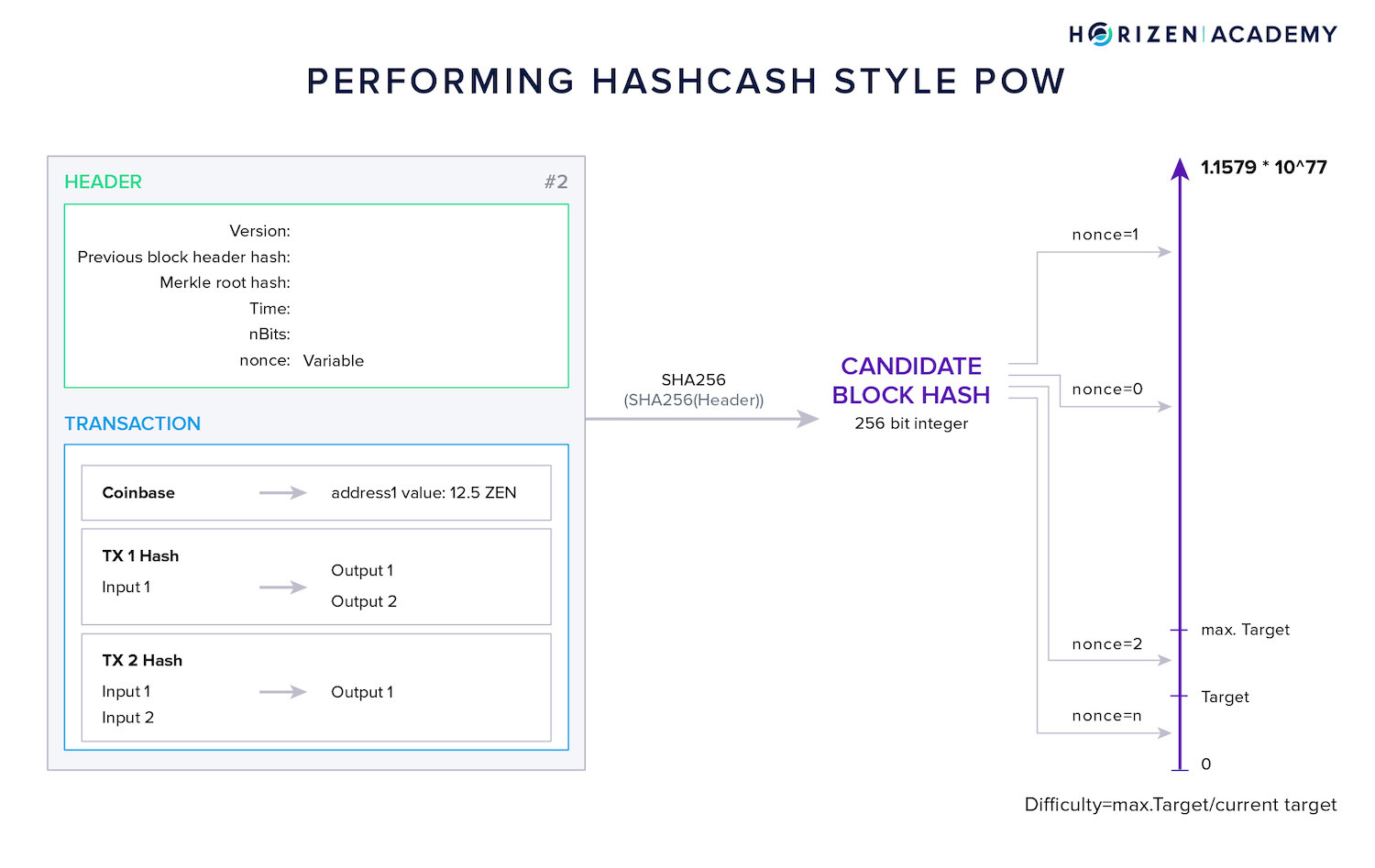
The graphic above shows the mining process in a Hashcash style PoW scheme.
The block header is repeatedly hashed using a different nonce each time. The header is hashed twice using SHA256 and the resulting candidate block hash is compared with the current target.
If it is greater than the target the nonce is discarded and the process starts again.
Once a miner finds a nonce producing a block hash less than or equal to the target, it is broadcast to the network, verified by all other nodes (including other miners) and appended to the blockchain.
The difficult is a different way to express the current target. The difficulty is a relative measure of the current target compared to the initial maximum target that is defined with the genesis block of a blockchain.
$$Difficulty = \frac{max. target}{target}$$
On the Bitcoin network, which has seen the biggest growth in hash power since its inception the current difficulty (at the time of writing) is about \(1.3 \cdot 10^{13}\), meaning it is 13 trillion times harder to find a block today, than it was when the protocol was launched.
What is the Role of a Miner?
The main job of a miner is to collect all transactions that are broadcast to the network.
The miner verifies if the transactions are valid according to the protocol and then places them in a data container - the block. The first transaction in a block is special, the coinbase transaction - sound familiar?
In the coinbase transaction, the miner rewards his own address with the block reward, 12.5 BTC or 12.5 ZEN at the moment.
Actually 7.5 ZEN on Horizen, as 10% of block rewards go to Secure Node and Super Node operators respectively, 20% to the Horizen Treasury.
These coins did not exist before.
Usually, one of the criteria that is used to check the validity of a transaction is if the sender has sufficient funds. The coinbase transaction rules are slightly different.
The protocol allows this first transaction to have no input, which means having no sender in this context. This is how the miners get to reward themselves for their work and how new coins are created.
Every ZEN or BTC in existence started out as a block reward.
After the miner includes the coinbase transaction, he places all other transactions he received in the block he is working on.
Usually, the miner adds the transactions in the order they arrived in.
In times of high network activity and full blocks, a block has a maximum file size, the block limit, miners might choose to include only the transactions with the highest transaction fees attached because they get to keep those as well.
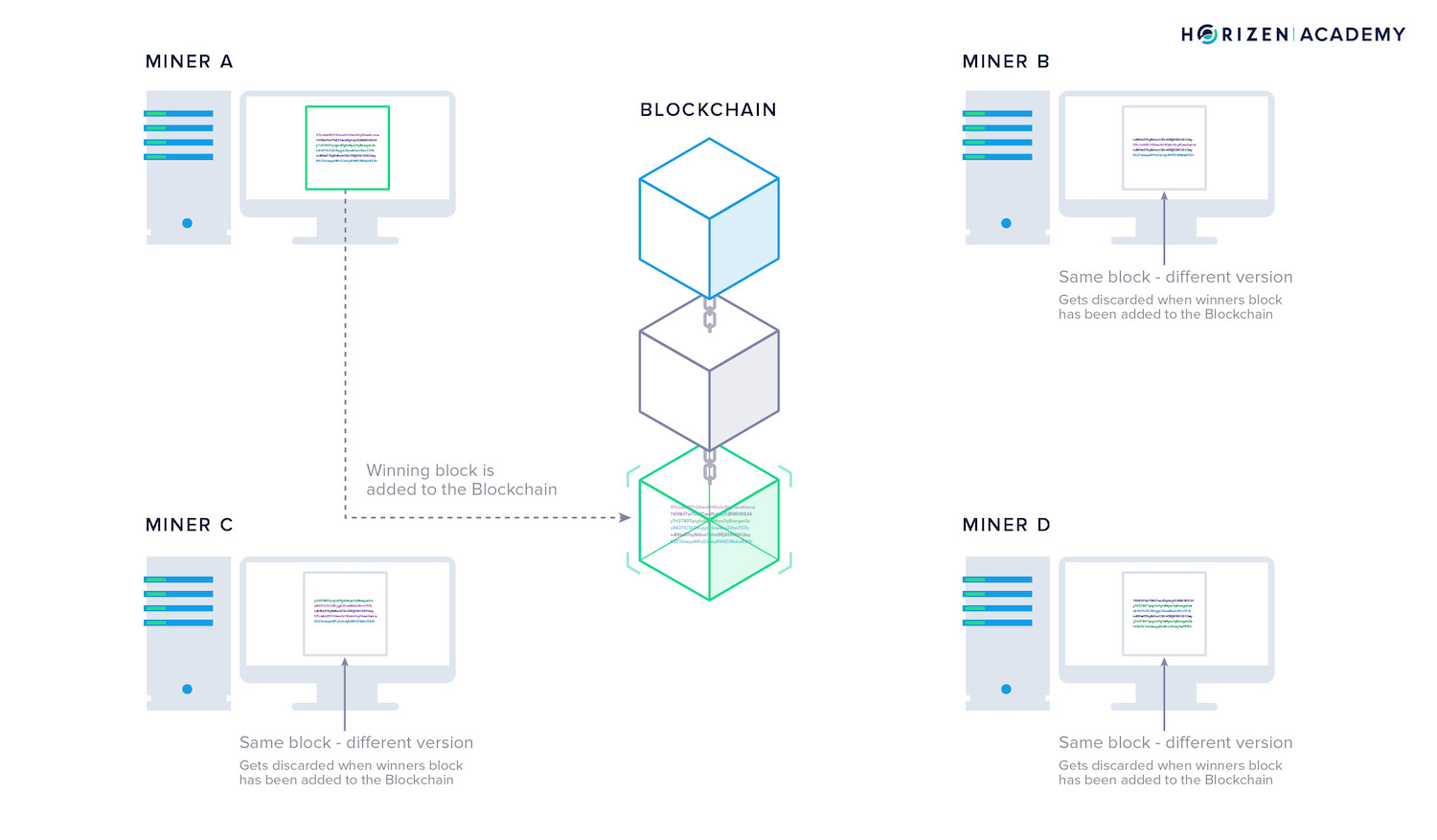
Many miners are working on a block simultaneously. Each miner has a slightly different block, either because he received the transactions in a different order than his competitors, or because he chose to include a different set of transactions based on the attached transaction fees.
The miner that solves the puzzle first, gets to extend the blockchain with his block, including the coinbase transaction that rewards him the newly created coins.
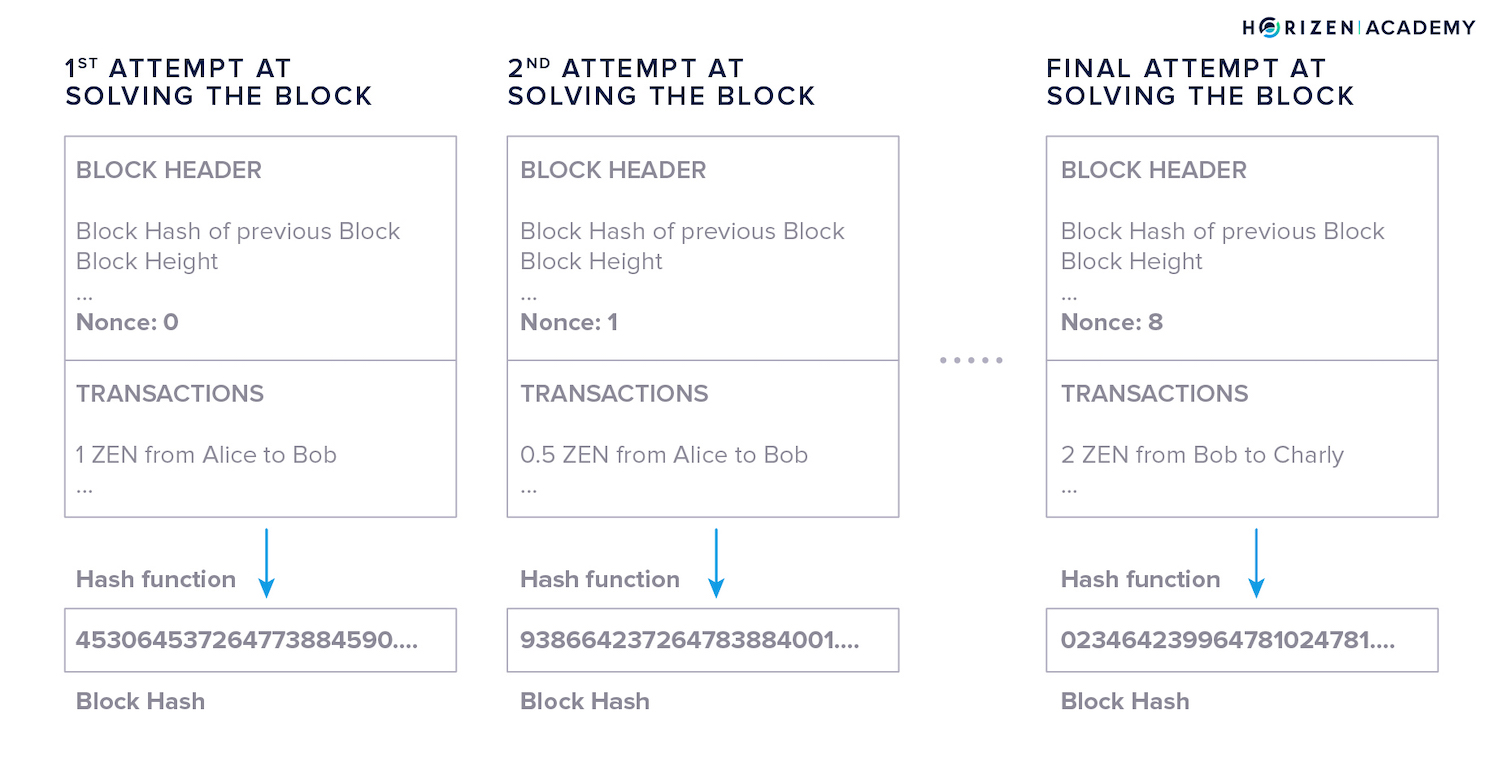
Finding a Nonce
So what is the puzzle that miners are trying to solve? This is where we need to talk about hash functions again.
One of the important properties of cryptographic hash functions is being pseudorandom. You must not be able to predict a change in the output that results from a change of the input.
As an example:
If you are hashing the input "1" and get the output "00002" and hash the input "2" afterward, the second output better not be "00004" but something like "73968", a seemingly random (pseudorandom) number.
In order for a block to be valid, its hash needs to be below a certain target. This target is basically just a number and the block hash has to be smaller than or equal to that number. In this context, you will often hear the term difficulty.
While the target is an actual value the block hash has to be below of, the difficulty is a relative measure of the current target compared to the highest possible target.
When the target is lowered, the difficulty is increased and it is harder to find a valid block hash.
Most of the data in the block is fixed, but there is a special data field in each block header, the nonce, that doesn't carry any important information.
Its sole purpose is to be a variable (a number used once), that the miner can put different values in, to change the output of the hash function - the block hash.
What follows is a trial and error approach of getting the block hash below the target. The block hash can be interpreted as a regular number. The lowest number a 256-bit integer can represent is 0, the highest number is \(1.1579 \cdot 10^{77}\)
115792089237316195423570985008687907853269984665640564039457584007913129639936
Imagine you were to calculate a hash for a random input that needs to start with one leading zero.
If there were only digits in the output the chance of getting it right the first time would be 1 in 10.
If the difficulty required the output to start with two leading zeros, your chance of getting it right the first time would be 1 in 100. And if the target was a difficulty of 6, chances would be 1 in 1,000,000.
With increasing difficulty, solving this challenge evolves into real work, especially as there is no shortcut to trying out a bunch of different inputs. If you would like to play around with a hash function you can do so here.
When a miner first attempts to solve the block, they will put a random value in the nonce data field.
For the sake of simplicity, let’s say the nonce value the miner starts with is “0”. The block hash will be a seemingly random value in the possible range of the hash function.

So the process looks like this:
- The miner uses the hash function to calculate the hash of the block - the candidate block hash as we named it in the graphic above. In the example, the block hash using 0 as a nonce doesn’t meet the target.
- The miner now increments the nonce by one and hashes the block again. The resulting hash is still above the target, so the miner increments the nonce once more. This happens over and over again.
- Finally, one of the miners will find a nonce n that produces the desired result: a block hash below the target.
The hash rate on the Horizen network is at 208.68 Mh/s at the time of writing.
This means that all miners combined try 208,680,000 different values for the nonce every second. You can check the current value here.
Miners can’t cheat this process of trial and error because of the properties of cryptographic hash functions.
 v
v
There is no way to calculate a valid nonce from the desired output because the hash function is a one-way function.
It’s also infeasible to approximate a valid nonce from prior outputs because the hash function is pseudo-random and you can’t predict changes in the output from changes to the input.
Every participant on the network can easily verify if the solution is valid because the hash function is deterministic and will produce the same result for every node that verifies the block. Performing a single hash operation is also very quick.
Block Time
Every Proof-of-Work protocol defines a block time, an interval within which a new block should be created.
With Horizen this is 2.5 minutes, with Bitcoin, 10 minutes.
When a miner solves a block he broadcasts it to the network immediately, because he wants to collect his block reward. This is why it doesn’t take exactly 10 minutes to create a new block. 2.5 minutes is the average time that it takes to find a valid nonce and in turn, a valid block hash.
Some blocks are solved quicker and some take a bit longer.
If more miners join the network and the hash rate increases, they will find a valid nonce faster on average. The protocol evaluates the average block time and adjusts the difficulty accordingly every 8064 blocks.
If it takes less time on average to solve a block the difficulty will increase, if it takes longer the difficulty will decrease.
How Does This Protect the Network?
By now, you know that it requires a huge amount of work to solve a single block in a blockchain. You also know that each block references the preceding block by including its block hash, therefore chaining them together.
You also know that changing one little piece of information in a block will alter its block hash completely.
If an attacker wanted to tamper with any record on the blockchain, they would have to find a valid nonce for the block they edited, as well as all the following blocks. The attacker would have to do all this by themselves, and at a faster rate than the network is performing the mining process.
The longest chain rule determines which branch of the blockchain is the valid one in case a fork occurs. As long as the attacker does not control a majority of the hash rate, he won’t be able to change the blockchain.
The Purpose of Miners
Now you might ask why it is necessary to make block production computationally hard if we want to continuously add blocks to the blockchain. The reason is that PoW is an efficient way to provide Sybil resistance.
Sybil-Resistance
In a Sybil Attack, an attacker creates a large number of malicious nodes in an effort to achieve some goal. In the blockchain context, this goal can be including malicious transactions in a block, censoring transactions from a given network participant or performing a double spend after a block reorganization.
Spinning up a node comes at a very low cost, so there is not much to prevent an attacker from creating a large number of them. The consensus mechanism represents an abstract form of voting on different versions of the transaction history.
If voting was tied to an IP address, an attacker could manipulate the vote easily by creating Sybil nodes. By tying the voting power to external costs, electricity and hardware, interfering with the voting process on blocks becomes much harder.
Providing Immutability
Not only does PoW prevent Byzantine actors from obstructing the block production process, but it also protects the history recorded on the blockchain from being tampered with. All nodes following the protocol of a blockchain will reject versions of the blockchain that do not have a chain of references form the current block all the way back to the genesis block, each protected with a Proof of Work.
Without a Proof of Work, this chain of references could be reconstructed at almost zero cost. Only by securing each link between two blocks with a large amount of spent electricity, the blockchain becomes immutable.
Without Proof of Work, it would simply be tamper-evident.
A node with access to the most recent protocol can verify the entire blockchain with all its transactions without having to rely on any external input.
It will start with the first block, reconstruct the Merkle tree of transactions to verify the Merkle root included in the block header is valid, validate if the block hash meets the target given the nonce used to produce it and finally moves on to the next block.
It can also compute the difficulty at any point in time as the rules for when and how the difficulty changes are part of the protocol.
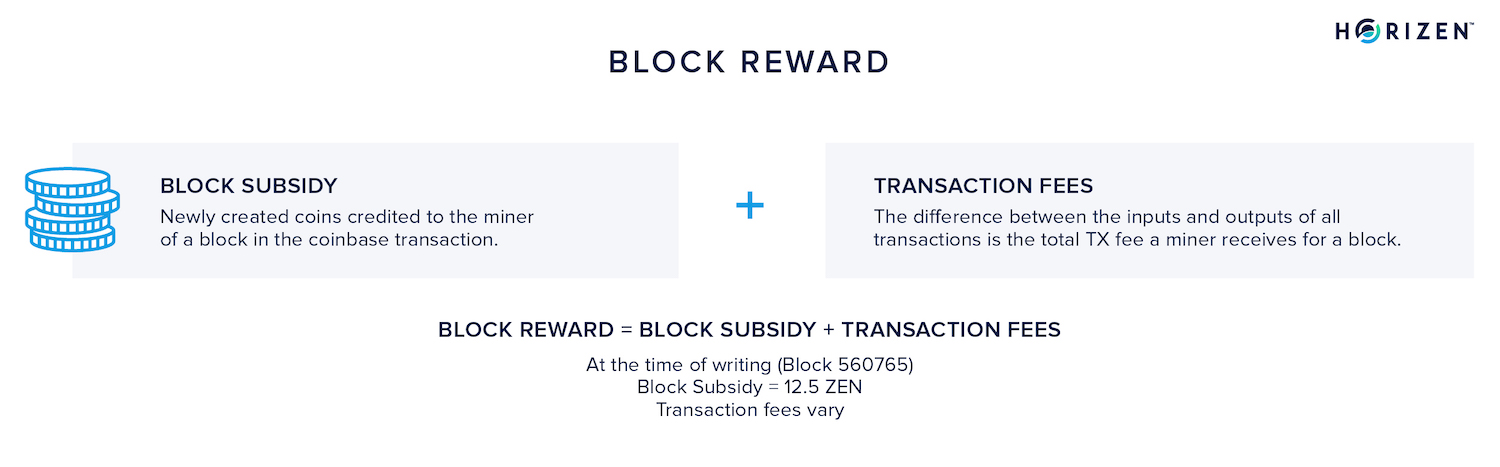
For their contribution to the network, miners are allowed to include the coinbase transaction. In this transaction miners are sending the current block subsidy and the aggregate transaction fees included in the block to a self-controlled address.
After the block reward maturation period ends this output becomes spendable. The block maturity interval for Horizen as well as Bitcoin is 100 blocks.
Mining Algorithms
Let's recap the defining properties of a "good" Proof of Work:
- Asymmetry: The Proof of Work needs to be hard to produce, but easy to verify.
- Optimization Free: An optimization free algorithm means that you cannot improve the efficiency of performing that task through software or algorithmic improvements.
- Amortization free: This means economies of scale that would render all mining pools besides the largest one irrelevant should not be possible based on the algorithm. (Other aspects of mining will always enable economies of scale to play out.)
- Independently Tunable Parameters: Certain parameters of the problem to solve by the miners should be easy to adapt to changing circumstances, e.g. an increase in hashrate.
Furthermore, the PoW needs to be pseudorandom so there is no shortcut to taking a brute-force approach to solving the task at hand. This also ensures that the block production time follows a statistical distribution with a constant average, ceteris paribus.
The PoW algorithm also needs to have independently adjustable parameters to account for changes in the overall hash power. To keep the block production rate constant as more hash power is added to the network the difficulty can increase.
On the Horizen network this difficulty adjustment is performed after every block.
$$ next-difficulty = last-difficulty \cdot \sqrt{\frac{150 sec}{last-solve-time}} $$
The algorithm needs to be deterministic so the verification of the proof is guaranteed.
Mining Hardware
In our article on PoW we introduced two metrics to assess computational hardness.
Space complexity refers to the memory intensiveness of the computation, while time complexity describes the reliance on the processor.
When a PoW algorithm involves creating large data sets in an intermediary step this will increase the space complexity. Other PoW algorithms barely require any memory as they involve repeated hashing of small amounts of data in the kilobyte range.
By concatenating many computations on this small data set the time complexity of the algorithm will increase, with the space complexity remaining constant.
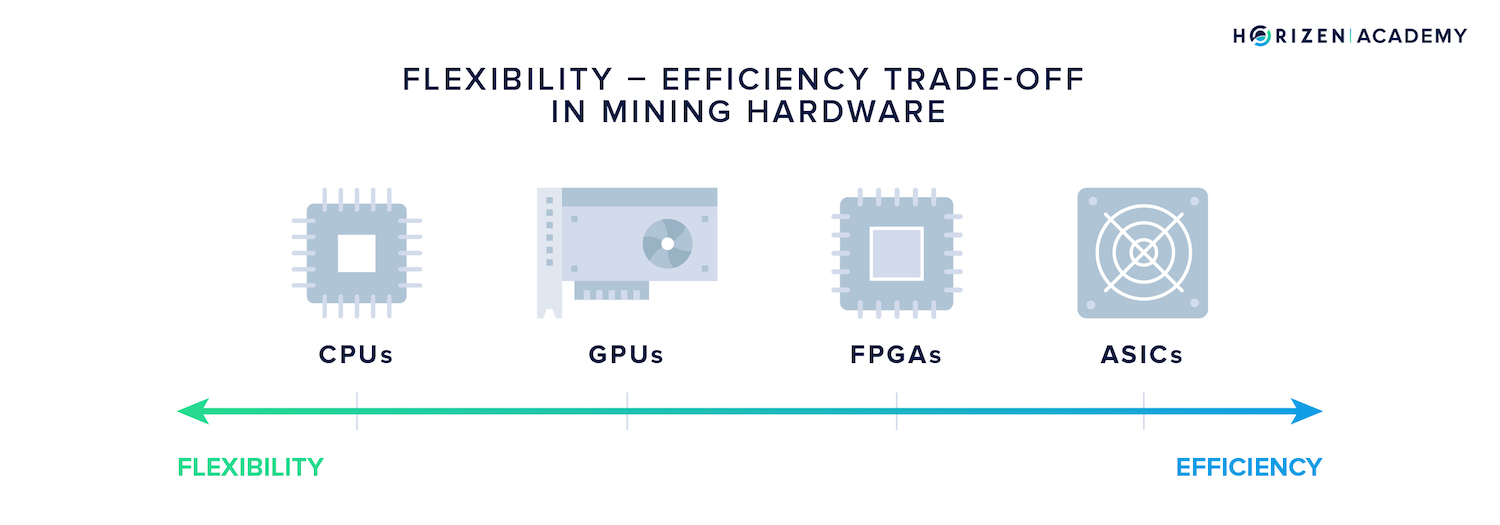
The Flexibility-Efficiency Trade-Off
When it comes to hardware there is a tradeoff between versatility and performance. A highly specialized chip architecture will allow a very good performance on one task, at the cost of being less versatile and vice versa.
The central processing unit (CPU) of a computer offers the greatest flexibility with regards to the types of computations it can perform, at the cost of being not very performant.
The graphical processing unit (GPU) is focused on tasks around image processing as the name suggests. It also includes more memory because computations on graphics tend to have a higher space complexity.
Field-programmable gate arrays (FPGAs) are meant to be configured for a specific task after manufacturing which allows a specialization of the integrated circuits depending on their application. After configuration they represent another step towards specialization at the expense of versatility.
As the name suggests, the Application Specific Integrated Circuit (ASIC) sits on the end of the spectrum on specialization and allows for the efficient execution of the tasks it was designed for.
From CPUs to ASICs
In the early days of cryptocurrency mining, people used the hardware they had at hand - desktop computers and their CPUs. In October of 2010, GPU mining became feasible when the first software utilizing the graphical processing unit for mining was released to the public.
People with a gaming setup were now at a serious advantage compared to CPU miners.
Mining started to become more lucrative and hence more competitive. People started configuring FPGAs to suit the requirements of efficient mining. The last major evolutionary step in mining happened in 2013 when the first ASIC designed for cryptocurrency mining was released.
ASIC Resistance
A number of different "ASIC resistant" mining algos were proposed but ASIC resistant algorithms are a myth - at least to some degree.
When a chip manufacturer designs an integrated circuit with a specific mining algorithm in mind, it will always perform better than a more versatile GPU.
More realistically, the assumption was that the cost to design and produce ASICs for certain algorithms was just not worth the marginal improvement in efficiency. While this assumption was certainly justified at the time many of the mining algorithms emerged, it didn't account for the rising valuations of cryptocurrencies that we saw in 2017.
This caused a range of ASICs being developed for different mining algorithms, including some that were thought of as "ASIC resistant".
ASIC resistance was mostly achieved by increasing the space complexity of the algorithm and thereby increasing the memory demand. High-bandwidth memory is a very expensive component in chip manufacturing.
A general increase in demand for high-speed memory technology such as GDDR6 and HBM2 made producing relatively cheap ASICs for memory intensive mining algorithms feasible.
The demand for ASIC resistant algorithms came largely from an interest in a decentralized mining economy resulting in a more decentralized distribution of newly minted coins. GPUs are more widely spread and accessible than the highly specialized ASICs.
Hence, a GPU-mineable algorithm would in theory lead to a wider distribution of new coins.
The demand for GPU mining was met with some projects changing their mining algorithm, rendering the highly specialized ASICs useless.
But changing algorithms mostly benefits large hardware manufacturers as they have the resources to develop ASICs for the new algorithm first. By sticking to an algorithm, smaller companies have the chance to design and produce mining hardware accordingly, which decentralizes the business again.
Today, we are past the peak of mining centralization. For a period of time around 2017 and 2018, Bitmain used to be the dominant manufacturer for mining specific hardware.
Since then, their market share has constantly decreased and new players have entered the scene.
Mining Professionalized
Besides using sophisticated and specialized hardware, mining has professionalized in other ways. Economic principles known for decades and centuries increasingly started to apply to the field.
The Need for Cheap Electricity
First, location factors are very important today, as the industry is highly competitive and electricity prices are an important factor determining if a mining operation is profitable or not. Miners settle in regions with very low electricity costs in order to gain a competitive advantage.
Mining Pools
Next, miners started to organize into mining pools. They prefer stable cash flows and have come up with mining pools to share the work and socialize the winnings. Mining pools have a centralizing effect and grant a lot of power to the pool operators.
Mining pool software could be configured to exclude transactions involving certain addresses - something that cryptocurrencies try to avoid at great cost.
Economies of scale are also starting to play out, which is not a bad thing per se.
A mining operation will always be more profitable when it gets bulk discounts on hardware or electricity and the price per square meter tends to go down when you rent or buy larger warehouses.
But large-scale mining operations operate in a highly competitive environment that leaves minimal margins when selling the mined coins. To cover operational costs there is constant selling pressure for these actors, which effectively makes it seem like coins are issued to the secondary market directly.
Mining Economics
When you look at the economics from a miners perspective you first need to think of the cost of the operation, then consider the potential revenues and lastly, derive an estimate of your profits.
CAPEX vs. OPEX
The costs can be divided into two categories, capital expenditures (CAPEX) and operational expenditures (OPEX):
- CAPEX are the cost of acquiring non-monetary capital like mining gear, racks, and property (if bought).
- OPEX are ongoing expenditures like wages, electricity cost for the rigs as well as cooling and property (if rented).
Setting up a mining operation will usually come with both capital and operational expenditures but depending on the circumstances it can be set up to tend towards being CAPEX or OPEX-heavy.
Hashrate vs. Price
The mining industry and the price of a given coin are arguably related to some extent.
First, the hashrate will follow the price, because an increase in price will increase the profit margin of existing miners and lead to them taking more hardware online.
Additionally, new entrants will join the network and try to get a share of the cake. This increase in competition and the accompanying decrease in margins leads to the mining cost tending towards the price of a coin, minus a small margin for the miners.
The trailing effect of the hashrate following the price comes with a delay and the delay when prices rise is greater than in a situation where prices decline. Ordering new mining gear and getting equipment live takes longer than taking hardware offline when prices decline.
The Fixed Issuance Schedule
Without the difficulty adjustment in place, a given amount of hashrate would always produce a fixed amount of coins. This would still allow for a fixed supply, but not a fixed issuance schedule.
This is an important differentiating factor when comparing cryptocurrencies with gold.
With gold, production will increase as prices rise. Less profitable, inactive mining sites are reactivated as the expected return on investment (ROI) becomes positive and active mining facilities increase their production. This effect also plays out the other way around.
When prices decline, mining facilities are lowering their production or closing all together. This dampens the volatility because the supply can increase or decrease in tandem with price. With cryptocurrencies production is constant and can not display this effect.
An economic term often used in the context of commodities like gold and other metals is the Stock-to-Flow ratio. It describes the amount of a commodity in circulation relative to the production rate.
Bitcoin was the first asset to ever allow not just for a predictable supply and issuance schedule, but also a predictable stock to flow ratio.
Mining Strategies
As we mentioned earlier, mining is a rather intransparent business, and cryptocurrency mining is no exception.
Miners can be one of three things: honest, rational or malicious.
- An honest miner will adhere to the rules of the protocol at all times.
- A rational miner will act to maximize profit, either by adhering to the protocol or deriving from it, depending on the incentives provided.
- A malicious miner will derive from the protocol to achieve their objective.
It can be assumed that the majority of miners are rational participants, meaning they follow the protocol as long as it is the most profitable strategy. Though some strategies have evolved that are used to gain an unfair competitive advantage - most notably selfish mining.
Energy Consumption in Mining
One of the biggest criticisms with regards to Proof-of-Work and the mining process is the large energy consumption.
Bitcoin is the blockchain that consumes the greatest amount of energy due to the immense hashrate on the network.
The University of Cambridge tracks Bitcoin Electricity Consumption through the Cambridge Bitcoin Electricity Consumption Index. While most other blockchains have only a fraction of Bitcoin's energy demand, they do consume a lot of energy.
This energy consumption is a necessity for securing the ledger.
Only by spending real world resources on securing the links between blocks, these references become costly to forge. So costly in fact, that after a reasonable confirmation time you can be certain an entry in the blockchain will not be reversed.
"Saving" Energy
The argument that blockchain consumes too much energy can be answered from different angles.
The criticism is often based on the premise that the energy is being "wasted".
When you pay for a commodity and use it to achieve a subjectively (and also objectively) valuable goal, mining cryptocurrencies, the energy is not wasted but used.
In fact, a lot of the energy used for Bitcoin mining might go to waste if miners weren't using it. This is true for certain regions in Canada, which have built massive hydropower plants and have to figure out how to use excess energy.
Another way to "save" energy, or better use under-utilized energy, is using natural gas. Instead of flaring it, it can be used to power gas generators, and those can power mining gear in return.
Utilizing Renewable Energy
Miners use an over-proportional share of renewables compared to the global energy consumption. As of December 2019 it is assumed that 73% of Bitcoin's energy consumption comes from renewable sources.
It is reasonable to assume a high share of renewable energy being used to mine other currencies as well. Oftentimes renewable energy is a lot cheaper than energy from burning fossil fuels.
Many regions that have focused on expanding their renewables production have regional oversupplies of energy, which leads to very low prices. Overall, cryptocurrency mining is a way for renewable energy producers to temporarily utilize energy that the grid cannot transport to locations where it is needed.
By mining with their excess energy, they can lower the financial risk of setting up a wind park, hydro dam, or solar park. PoW might therefore pose a net positive for the global energy footprint.
Efficient Electricity Export
Lastly, using energy to mine is a great way to export cheap electricity. Transmitting electricity over long distances is highly inefficient. A mechanism used in the past to utilize stranded energy was performing energy-intensive but location independent services in these regions.
One example is Iceland, which has access to large amounts of clean energy due to being located in a geothermally active region. Iceland generates about 70% of its electricity from hydroelectric sources and 30% from geothermal sources.
Iceland has pivoted into a highly energy intensive industry due to this fact, namely aluminum production.
“We are based in the middle of the North Atlantic Ocean. We are not connected to the mainland Europe grid,” said Bjarni Mar Gylfason, chief economist for the Federation of Icelandic Industries. “So we export energy in the form of aluminum." - Henry Chu, Los Angeles Times, Iceland Divided Over Aluminum’s Role in its Future
Cryptocurrency mining has the potential to even the global energy-price hyperplane through miners settling in regions where electricity is abundant.