What are Zero-Knowledge Proofs?
Zero-knowledge proofs are ushering in a new era of dapps and blockchains that offer greater scalability and privacy through advanced cryptography.
In this article, we go into detail about what Zero-knowledge proofs are and how this technology is bringing mainstream adoption to Web3.
What are Zero-Knowledge Proofs?
A Zero-Knowledge Proof is a form of cryptography that enables one party in a transaction, the prover, to prove that they have knowledge of information that confirms a statement to be true to another party, the verifier, without revealing what that information is.
For example, if a person wishes to proof that they are over the age of 18, rather than issuing a credential that contains all kinds of personal information as a form of identification, with ZKPs, the prover can construct a ‘proof of correct computation’ that confirms any aspect of their identity that they wish to verify. For instance, that they are over the age of 18 or that they have a driver's license).
The specific form of ZKP applied for this use case is called zk-SNARKs, Zero-Knowledge Succinct Non-Interactive Argument of Knowledge.
What are zk-SNARKs?
With zk-SNARKs, ‘non-interactive’ simply means that the code for constructing or verifying proof of computation operates autonomously, without the need of human intervention.
In another example, let’s say a client, the prover, needs to prove to a broker, the verifier, that they have a certain amount of money in their bank account without revealing their finances.
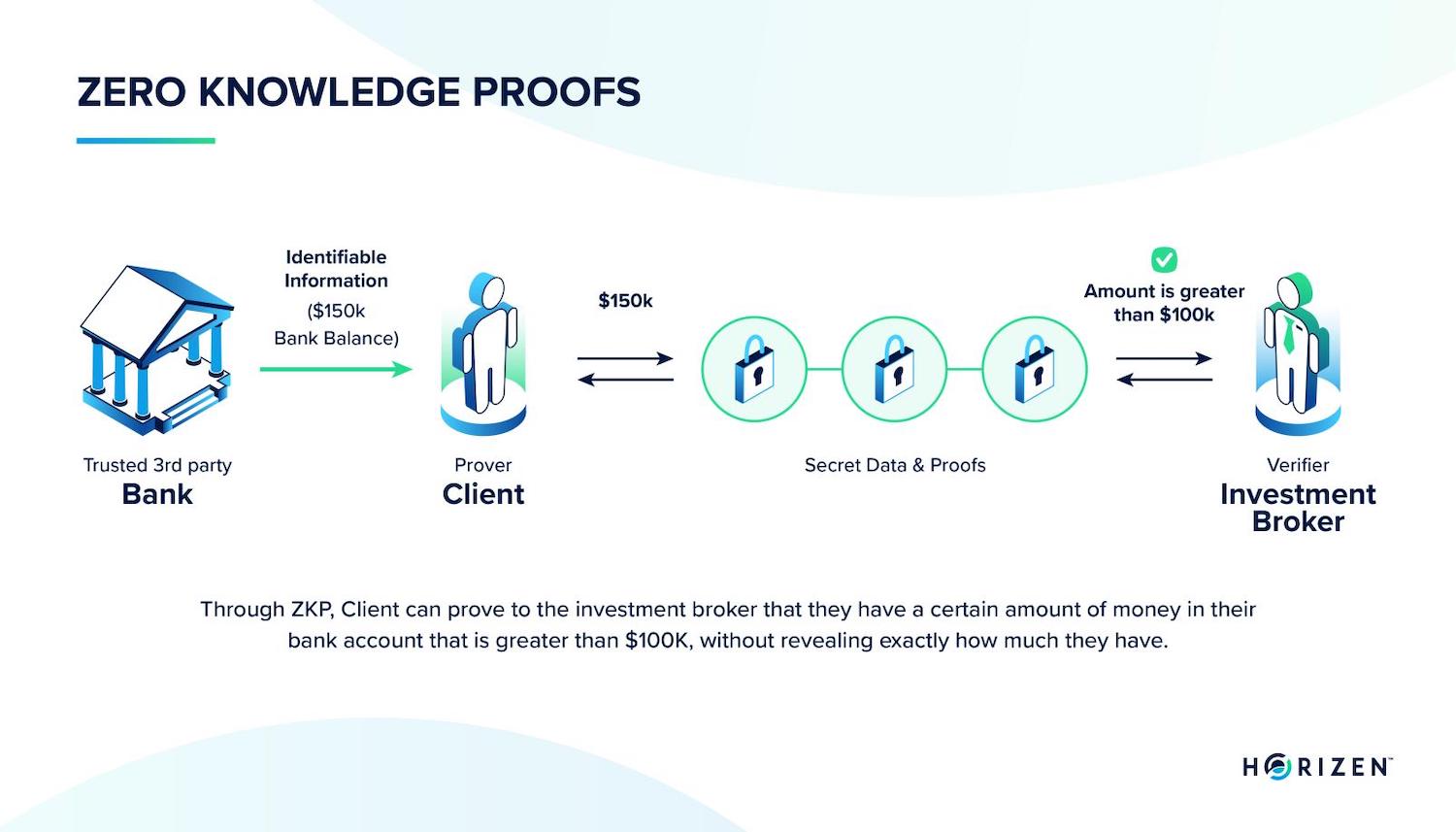
Using zk-SNARKs, the broker can simply verify that a computation was run on the blockchain in which the client solves a series of challenges issued by a simulator, which correctly confirms the statement to be true (e.g. bank value > $100,000).
zk-SNARKs have been adopted by a variety of blockchain networks to improve privacy and scalability.
Most notable of these blockchains is Horizen, a zero-knowledge enabled network of blockchains.
What Are the Properties of Zero-Knowledge Proofs?
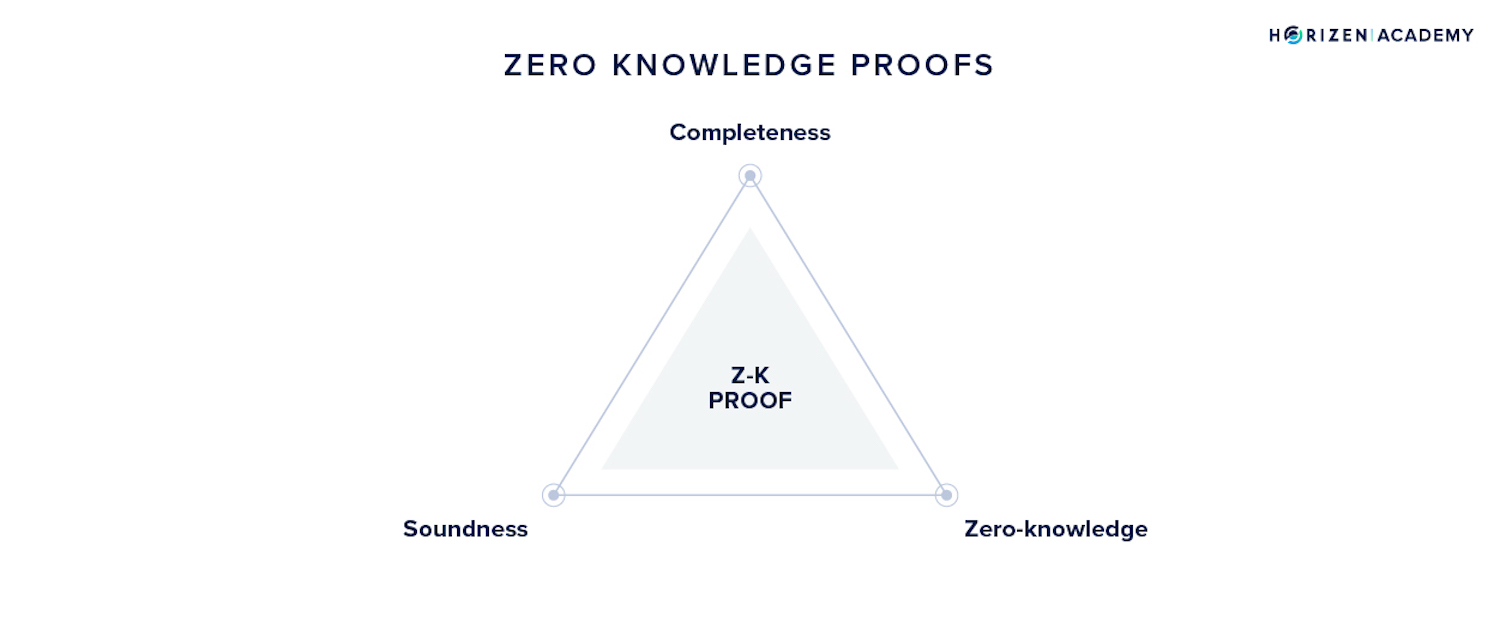
A zero-knowledge proof algorithm must contain the following 3 properties:
- Completeness - If a statement is correct, and the prover and verifier both follow the correct protocol, then the verifier should accept the proof as true.
- Soundness - If the statement is false, then the verifier will not be convinced by the proof even if they follow the protocol.
- Zero-Knowledge - If the protocol is followed by the prover and the statement is deemed to be correct, then the verifier should be convinced of the prover’s statement being true, even though they have no knowledge of any other information besides the provided proof.
Use Cases of Zero-knowledge Proofs
The potential for zero-knowledge proofs are virtually unlimited. Here are some examples of how ZKPs can be applied to solve problems and create new opportunities in tech and the traditional economy
Healthcare
One way ZKPs could be applied is that a patient can show proof of correct computation that allows the verifier to confirm that they are eligible to receive a certain treatment or medication without revealing their specific health records for a problem posed to the prover.
ZKPs can also enable pharmaceutical products to have been properly audited without exposing sensitive information that might comprise intellectual property or confidential patient data.
Financial Services and Defi
ZKPs can help users provide proof that they are qualified to use certain financial products or should be granted a loan without revealing their age or net worth.
Real World Assets
Real world assets represent the next frontier for mainstream crypto adoption.
In the past 3 years, Defi protocols like Aave and Uniswap have laid the groundwork for individuals and entities to trade and lend their digital assets using smart contracts that are secure, trustless and highly efficient.
We’ve also seen the advent of NFT marketplaces like OpenSea enable seamless trading of non fungible digital assets primarily representing artwork.
While some see these innovation as little more than tools for speculation, there exists a massive amount of untapped potential for larger market players such as corporate entities, foundations and even government agencies to tokenize assets in the real world in order to plug them into these Defi protocols for the purpose of lending, licensing, trading and transferring ownership in a more efficient and secure manner.
One of the key missing components in this next phase of adoption is privacy. Mainly, how do we enable highly regulated institutions to tokenize assets that may contain sensitive or proprietary information on a public blockchain without exposure to legal or commercial risks?
Privacy preserving technologies like zk-SNARKs can solve this problem by creating a mechanism that enables the authenticity of an asset to be proven without revealing any compromising details about the asset.
This enables entities to monetize and commercialize real world assets like accounts receivables, trademarks, IP or even machinery while protecting information from unnecessary disclosures.
ID Verification - For Example: Proof of Age
Let’s say a prover wants to prove to a verifier, a brokerage service, that they are over the age of 18 without revealing their exact age.
The prover would need to construct a ‘proof’ that is generated based on identifiable information that has been endorsed by a trusted third party (i.e a bank or government agency).
The process of constructing a proof involves correctly solving a series of challenges issued by a hash function simulator that proves knowledge of a particular piece of information. The role of the trusted third party is not only in authenticating the private information, but in also establishing the parameters for the challenges issued.
Think of this like the rules to a game in which the outcome is to be verified. The parameters are shared with the verifier so that they too can understand the rules and know that the prover played the game according to those rules.
One way to think about the challenges posed by the hash function simulator is to compare it to the security questions that your bank asks you in order to verify your identity before opening a support case or authorizing a large transaction.
The more questions about your previous transaction history, old home addresses or phone numbers that you answer correctly, the more likely it is that you are in fact the rightful owner of the account.
Once the challenges have been solved, a proof is constructed and sent to the verifier. The proof is simply a certificate acknowledging that the questions posed were answered correctly. The next step is for the verifier to receive the proof and then use a custom algorithm to verify the correctness of the proof based on the parameters provided earlier.
This custom algorithm will essentially re-run the sequence of challenges issued against the answers given in order to confirm that they were answered correctly, all without revealing any private information to the verifier.
Once confirmed, the verifier can acknowledge that the statement about the prover, that the prover is over 18, is correct.
Under a ZKP proof system, an example of a proof statement for the “over 18” use case could look something like this:
- I possess a credential A,
- matching schema B,
- containing field C,
- where C contains a numeric value > 18,
- and the credential contains a cryptographic commitment to a link secret D that I know,
- and the credential has an revocation index, E, which I know,
- in revocation registry F,
- and the credential’s status in F is unrevoked
- and I know a signature G,
- from issuer H,
- endorsing that value C in the context of A, B, D, E, and F.
This statement is verified by the ability for the prover to show possession of ‘credential A’ through correct computation rather than by revealing the information.
‘Issuer H’ is the trusted 3rd party who endorses credential A using their signature.
DeFi KYC
ZKP-based ID verification methods could enable Defi platforms or other public blockchain applications to prove compliance to regulatory bodies and institutional clients without performing traditional KYC procedures that require the collection and storage of user data or without revealing the prover's full identity.
Using zk-SNARKs, a user interacting with a DEX could prove certain facts about themselves, that they are over a certain age and have over a certain amount of money in their bank account, without revealing any details about their identity or even the source of the identifiable information.
A large institutional trading firm or bank may not always want to reveal themselves as the trusted third parties for their clients (i.e provers) who are looking to conduct KYC verification on-chain, as it may lead to certain wallet addresses being targeted by hackers or frontrun by trading bots.
Trusted third parties could exist anonymously on the blockchain and provide the private information and parameters necessary for constructing a proof.
One way this could work is using zk-SNARKs to prove that an exchange or bank is a legally registered entity without their name or any other identifiable information being revealed.
A proof constructed by a prover could then be submitted by DEX’s to regulators in order to show that all of their users are already identified by a trusted third party and meet certain requirements for using their services.
Hiring
Labor markets could always benefit from more transparency, yet in many circumstances that can conflict with the need for companies to maintain competitiveness in their compensation.
Likewise, employees often want to know how much their colleagues are getting paid, yet for legal reasons this information can not be disclosed.
ZKPs would allow employers to prove that an employee's salary is lower or higher than the average of their colleagues without revealing how much their colleagues are getting paid. Companies could also use this technology to prove that they pay above market salary without disclosing how much their employees earn.
Marketing and Surveys
Zero-knowledge proofs could be used to allow customers to opt into online services and authenticate themselves without revealing who they are. This could open the doors to privacy enabled loyalty programs.
ZKPs can also enable anonymous surveys that allow research organizations to source people who fit a specific criteria but without needing to record their data.
Voting and Governance
ZKPs allow you to prove that a person or entity is qualified to vote for something without revealing who they are. This can come in handy for issues that are sensitive in nature and require anonymity yet still need some form of authentication to ensure that there is no manipulation in the voting process.
Blockchain Scalability
What zk-SNARKs do is compress the amount of data that a node needs to process in order to validate that transactions are correct before being confirmed into the next block.
On Horizen, zk-SNARKs allow a prover, the sidechain, to prove that a transaction is valid to a verifier, the mainchain, without the mainchain nodes knowing the details of the transaction, for example, addresses or values transferred.
The sidechain does this by first validating transactions in its blockchain as normal, then, constructing a proof which is essentially a certificate that proves that the transactions within the sidechain have been correctly validated based on a standard process that is recognized by the mainchain.
This certificate is used to accurately represent the state of the sidechain or chains, for example account balances and total values in each sidechain, while containing far less data compared to the tens of thousands of transactions it represents altogether.
The nodes on the mainchain then use a special algorithm to validate this certificate just like they would for any other transaction.
If the algorithm confirms that the certificate/proof is correct, the mainchain nodes will then take this as evidence that the transactions in the sidechains have all been correctly validated without needing to perform the validation process themselves.
In other words, instead of the mainchain nodes validating every single sidechain transaction, the mainchain can simply verify proof of computation for tens, to hundreds of thousands of sidechain transactions within a single block.
Compared to the 1,500 transactions per block limit on Bitcoin or 200 transactions per block limit on Ethereum, it is clear that zk-SNARKs can significantly scale the number of transactions processed by a blockchain without compromising security or decentralization - win win.
Different Approaches To Privacy-Enabled Scalability
There are other blockchains that have caught on to the idea that ZKPs can be a tool for achieving scalability through privacy.
These networks have adopted a popular version of zk-proofs called ZK-Rollups.
ZK-Rollups are an innovation originally launched on Ethereum that enables L2 transactions to be transmitted and verified by the Ethereum network without the Ethereum nodes knowing the details of each transaction.
It is designed to offer greater scalability to the Ethereum network by only requiring the Ethereum nodes to verify the proof of computation rather than the transaction data itself.
While L2s like Loopering leverage ZK-rollups to achieve scalability on the Ethereum network, layer 2 networks are limited in their ability to operate with the same flexibility as an independent, layer 1 blockchain.
| Ethereum L2 ZK-Rollups | Horizen Sidechain zk-SNARKs |
| ZK-Rollups allow faster settlement of L2 transactions on the Ethereum L1 using only proof of computation. | Layer 1 sidechcain transactions can be settled directly on the sidechain because it is an independent blockchain. Withdrawals from the sidechain to the Horizen mainchain are conducted on an as-needed basis. |
| The Ethereum network must verify proof of computation for batches of L2 transactions. This requires submission of some limited information about each transaction to the Ethereum network, reducing scalability. | The Horizen mainchain only needs to verify the state of the sidechains periodically using cryptographically authenticated certificates - powered by zk-SNARKs. There is no need to push sidechain transaction data to the mainchain unless a specific withdrawal request is made. |
| L2s are considered off-chain scaling solutions for Dapps. Layer 2s are not independent blockchains, and are therefore less secure and rely on the Ethereum network for final transaction settlement. | Horizen sidechains are independent blockchains that can operate their own consensus mechanism and can validate and settle transactions independently. |
Horizen is also able to implement ZK-Rollups to make sidechains operate like a layer 2 would on Ethereum. However, Horizen believes the current implementation provides developers with greater flexibility and security because of the ability to operate their own independent, consensus agnostic sidechains.
In Conclusion - Zero-Knowledge Proofs
As a zero-knowledge enabled network of blockchains, Horizon’s decentralized ecosystem is designed from the ground up to power the proliferation of all kinds of unique use cases for preserving private data while authenticating information.
We believe zero-knowledge proofs are the next frontier for blockchain innovation, which is why Horizen is leading the charge in leveraging this technology to help push web3 further towards mainstream adoption.